
From China, With Love
Lest anyone think that D-Link is the only vendor who puts backdoors in their products, here’s one that can be exploited with a single ...
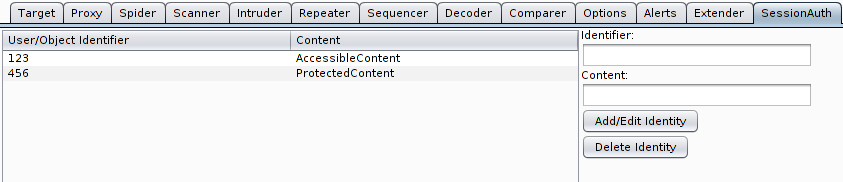
Burp SessionAuth Extension
Overview Normally a web application should identify a logged in user by data which is stored on the server side in some kind of session ...

Android Hack-Tool Steals PC Info
Over the weekend, Yeh, one of our Security Response Analysts, came across some interesting analysis on a Chinese language forum about an ...

The most sophisticated Android Trojan
Recently, an Android application came to us for analysis. At a glance, we knew this one was special. All strings in the DEX file were en...

Cracking Credit Card Hashes with PowerShell
As penetration testers, we are frequently engaged to do penetration tests for PCI compliance. As a part of these penetration tests, w...

Stupid Little IPv6 Tricks
With the IPv6 Summit on Friday, various IPv6 related topics are of course on my mind. So I figured to put together a quick laundry list o...

Steps Toward Weaponizing the Android Platform
The mobile and tablet market have been flooded by millions upon millions of Android based devices. I wonder if Ken Thompson or Dennis Ritch...
Flexible Home Layout
Downloads[two]
Media[left]
Books[right]
Photos[carousel](6)
Accessories[combine]
Zebronics
Advertisements

Popular Posts
-
Many Facebook users were assaulted by the following message earlier today, seemingly shared by their online friends: There is a vi...
-
Classified sites are really great money saver and you can contact directly your audience. You can save lots of money by using free classifie...
-
Facebook Touch , is a third-party Facebook app for your windows 8 devices. It is fast and simple windows 8 app to access your facebook acco...
-
Anonymous What is Information security? Security means surety of not breaching personal information. It is also known as safegu...
-
IPB (Invision Power Board) all versions (1.x? / 2.x / 3.x) Admin account Takeover leading to code execution Written on : 2013/05/...
-
A s we enter June, we inch closer towards Microsoft’s major Windows 8 release. The operating system has gone through several levels of de...
-
Introduction : Joomla! as Stable-Full Package is probably unhackable and If someone tells that HACKED Joomla, talking rubbish!!! But p...
-
DES(Unix) Example: IvS7aeT4NzQPM Used in Linux and other similar OS. Length: 13 characters. Description: The first two characters are...
-
Apache Tomcat 6.x / 7.x Denial Of Service http://packetstormsecurity.org/files/118615 Apache Tomcat Security Bypass http://packet...
-
Today we will Learn CPANEL cracking or Hacking i.e gaining password for port no 2082 on website first of all we need a cpanel cracking s...








.jpg)