How to hack Facebook via Sniffing ?
http://kingofdkingz99.blogspot.com/2012/03/how-to-hack-facebook-via-sniffing_19.html

How to hack Facebook via Sniffing?
Hi all users, after receiving your mails that most of facebook hacks
doesn't work anymore we have searched and tested and posted some of most
popular facebook hacking techniques but still I think doesn't work for
you so finally we've found this technique working 100% for hacking
facebook and today we're here to let you know how to do it. So you want
to hack Facebook, eh? Before we begin learning how to sniff and start
ARP poisoning, let's first begin with this: this tutorial was designed
for educational purposes--only! I take no responsibility in whatever
damage this may cause to those who wish to participate in this act of
hacking! That being said, if you still wish to continue in learning how
to get into someone's Facebook without them knowing, proceed along.
There are a couple of terms you will have to know before we begin. This
is so that you don't find yourself scratching your head midway through
this post wondering what the @$%# I'm talking about. Please understand
the following terms and they're respective definitions before
proceeding.
- Cookie: A cookie is just one or more pieces of information stored as text strings on your machine. A Web server sends you a cookie and the browser stores it. The browser then returns the cookie to the server the next time the page is referenced. Cookies are essentially utilized so that the website can remember certain aspects of that particular website so that when you return it loads the page faster.
- ARP Spoofing/Poisoning: ARP stands for Address Resolution Protocol and is a telecommunications protocol used for resolution of network layer addresses into link layer addresses, a critical function in multiple-access networks. It's the "guy" behind the scenes that stands in the middle of all the network traffic, takes in the requests of other computers on the LAN, and returns valuable information/answers. How do you think you get your IP address when you look up ipconfig in CMD? Your computer sends out a request to extract its IP address and the ARP essentially gives you the IP address for your computer. The act of "spoofing" or "poisoning" the ARP, as you probably can already tell, is a very dangerous protocol. By doing so, you are enacting what's called a "man-in-the-middle-attack", MITM for short. When you poison the ARP of a computer within a LAN, you are making yourself the ARP. In other words, all the requests the computers in the network make come directly to you and the answers go directly from you. More on this later.
- Packet(s): Packet, or packets, are a formatted unit of data carried by a packet mode computer network. They contain literally a million variety of information and provide useful methods in transmitting/receiving requested information. For example, let's take a look at sending an email. On the Internet, the network breaks an e-mail message into parts of a certain size in bytes. These are the packets. Each packet carries the information that will help it get to its destination -- the sender's IP address, the intended receiver's IP address, something that tells the network how many packets this e-mail message has been broken into and the number of this particular packet. The packets carry the data in the protocols that the Internet uses: Transmission Control Protocol/Internet Protocol (TCP/IP). Each packet contains part of the body of your message. Hopefully this gives you a general idea of how packets work and what they provide for both your computer and the internet.
- Sniffing: Sniffing is usually implied to sniffing network packets. Packet sniffing is the act of eavesdropping on another computer's packet transfer and capturing (saving) those packet transfers for analysis. Though this sounds malicious and wrong, packet sniffing is used widely around the world today for a number of beneficial reasons. But yes, you are correct, just like everything else there are both good and bad intentions for sniffing. An analysis of "sniffed" packets can often times to be used to pick out abusive/malicious acts within a network. An analysis can also provide the "sniffer" to pick out what the slave has been doing and what kind of information the slave's computer has been sending/receiving. Again, just a general definition but you get the picture.
Please read through the definitions and familiarize yourself with the
terms before asking what certain things mean here. You can't expect to
know every and anything without doing some homework. Trust me, knowing
these terms will not only save you time but also give you the benefit of
becoming more knowledgeable about basic network definitions Victoire
Software
The following is a comprehensive list of the software you will be
needing for this practice. I've given the links to their home pages
where you can download the software for free.
- Mozilla Firefox: http://www.mozilla.org/
- Web developer add-on for Firefox: https://addons.mozilla.org/en-US/firefox/addon/web-developer/
- Cain and Abel: http://www.oxid.it/cain.html
- Wireshark: http://www.wireshark.org/download.html
Sniffing Your Way In
Now that you're generally familiar with some basic network definitions
and have downloaded the required tools to effectively sniff packets, let
us begin. Go ahead and open up Firefox and log into your Facebook
account. You should be able to see the "cookies" option in the
upper-left corner of the toolbar. Click on that and select "View Cookie
Information".
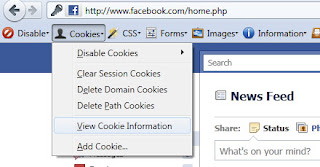
You should now see a collective group of information all in regards to
the cookies saved on your computer for Facebook. The main cookies are
the c_user cookie (which identifies a person uniquely) and datr cookie
(which contains important information for the specified c_user). Our
goal in sniffing into someone else's Facebook is to trick the browser
and the computer into thinking that we are someone else. How do we do
this? By manipulating cookies to disguise ourselves. Essentially we are
swapping our actual Facebook cookies to that of the slave's so that when
we log back into Facebook, it will think we are the slave rather than
ourselves. Not too hard to understand, right? Blink
Go ahead and close out of Firefox for now. Next, go and install Cain and
Abel. Throughout the installation process, the setup wizard will ask if
you want to install the packet driver WinPCap--go ahead and install
this. Once you have successfully installed Cain and Abel, open the
program. Now follow these steps exactly:
- Click on configure on top and select your Network card. Mostly its the one with an IP address Tongue.
- Next click on the start/stop sniffer on top as shown below in green square.
- Once you start the sniffer, goto the sniffer tab in Cain, right-click and click scan MAC address as shown below!
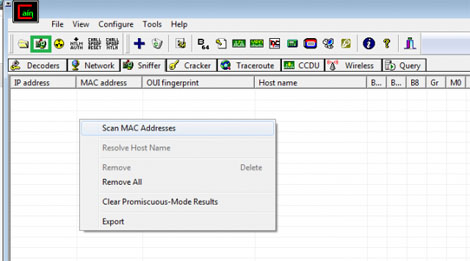
Depending on your computer and your network population this process can take a couple of minutes. Once it's complete, however, you should be able to pull up a list of computers on your LAN. One cool thing you can do here is right-click one of the computers and find out the computer name. Now it's time for the attack! What was the name of the attack again? Anyone? Did you forget already? Ah, yes, the MITM attack!
Again, follow these steps accurately to effectively spoof the ARP :
- First Click the APR tab below in cain.
- Click the white screen in the top frame
- Click the blue plus on top.
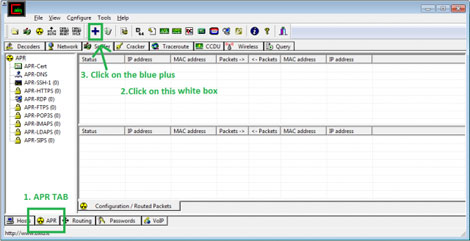
You should get a list of all the devices on the left and a blank screen on the right. In the left screen you should select the router IP. And in the right box, select the computers you want to target. To be safe its better to target one computer. But if you want some real fun then select all the computers on the right frame Hehe. Press "Ok". A caveat in selecting a large amount of computers, however, is that your computer may not be able to handle all the network transmissions and therefore lose some packet captures. Also keep in mind, however, that if someone is working in the router or is monitoring/analyzing the router and actually knows what he/she is doing, they could immediately detect that you are ARP poisoning the router. So be careful! You can get caught.
All the computers should have populated the top-frame. Now select the whole list and click on the nuclear button (top left of Cain, bolded box in the picture below).
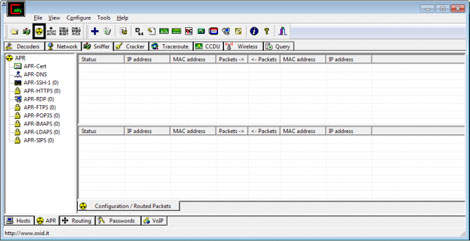
And you're done! You've successfully poisoned the ARP of the computers
you've selected and you are now the "middle-man" between your slave's
computer and the router to the internet. But wait just a second--we
can't get into the slave's Facebook just yet! All we've done so far is
established ourselves to be the "middle-man". We have to now capture
some packets, swap cookies, and voila! We're in.
Now we will open up Wireshark. Follow the steps below :
- Open up wireshark
- Go to "Capture –> Interfaces" in the top menu and select your interface. It’s usually the one which has an IP address and a certain number of packets flowing through it.
- Next go to "Capture" and click on "Start".
It should look something like this.
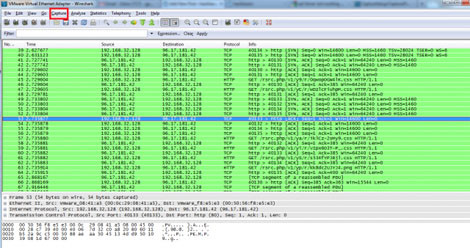
This window has all the packets sent from the slave’s/victims’ computer
to the router and all the packets sent from the router to the slave.
Next in the filter type “http.cookie contains datr”. You ask why? Because, when a user logs in to facebook, he is given some cookies which is unique to him. If we replace our cookies with the slave’s cookies, we can login to his account as then facebook wont know the difference.
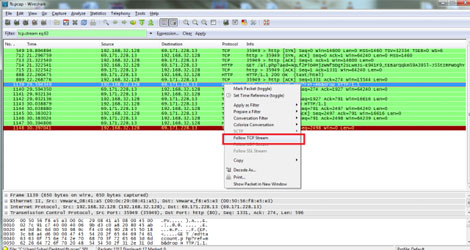
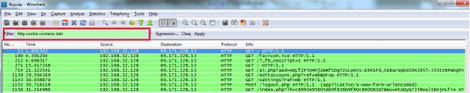 After filtering the cookies out, right-click on any one of them and click on "Follow TCP Stream".
After filtering the cookies out, right-click on any one of them and click on "Follow TCP Stream".
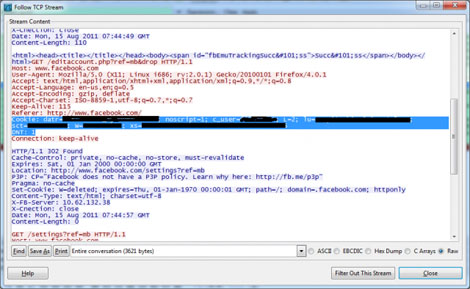
In the TCP stream look for the line "Cookie: ( and all cookie names)". If it doesn't show up, select some other packet in Wireshark and click on "Follow TCP Stream" for that particular cookie. You can see the source IP and destination IP in Wireshark. So if you have more than one source IP, then you know you have the cookies of more than one account on your LAN. This is what I got when I did it.
Next in the filter type “http.cookie contains datr”. You ask why? Because, when a user logs in to facebook, he is given some cookies which is unique to him. If we replace our cookies with the slave’s cookies, we can login to his account as then facebook wont know the difference.


In the TCP stream look for the line "Cookie: ( and all cookie names)". If it doesn't show up, select some other packet in Wireshark and click on "Follow TCP Stream" for that particular cookie. You can see the source IP and destination IP in Wireshark. So if you have more than one source IP, then you know you have the cookies of more than one account on your LAN. This is what I got when I did it.

You now have the slave's cookies for his/her Facebook. The main ones we
need to focus on are the datr cookie, c_user cookie, lu cookie, sct
cookie, w cookie and xs cookie. Now open up Firefox and go to Facebook.
If you're logged in, log out so that you're at Facebook's home page.
Click on the "Cookie" option in the toolbar (as like before) and do the
following in this exact order.
- Clear session cookies.
- Delete domain cookies.
- Delete patch cookies.
Note :-
If you don't do the steps in that same order, this will not work!
If you don't do the steps in that same order, this will not work!
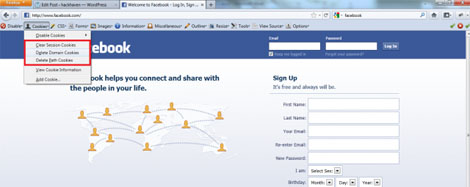
Note :- Once you do this, reload the Facebook page (http://www.facebook.com). This is to ensure that you are loading the Facebook page clean without any pre-existing cookies.
Now login to your account with your username and password. After logging in, click on cookies in web developer add-on just like before and click on “View Cookie Information”. You should see all of your Facebook cookies now. Any ideas what we do next? I suspect you know by nowOui.
Click on “Edit Cookie” for each cookies there and replace the cookie value with the value you got through Wireshark. If you didn't get all the cookies in Wireshark, it's OK! But mainly, you should look to replace the datr cookie, c_user cookie, lu cookie, sct cookie, w cookie and xs cookie.
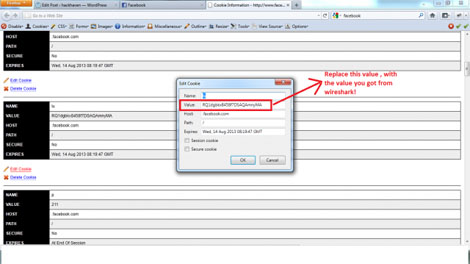
After you have swapped cookies, go ahead and refresh the page. Voila!
You should now be logged in as your slave rather than yourself.
Congratulations, you have successfully "hacked" your way into someone
else's Facebook! Again, please keep in mind that this only works for
computers within your LAN. So if you're at home, you can only get into
the Facebook of people who are connected at home. No, you cannot hack
into the Facebook of someone across the worldNon.
I hope you guys have enjoyed this tutorial! Please feel free to leave me
any questions below or PM me with any issues you have. I'll try to
respond and reply at my soonest convenience.







Hey Joe ! You got unbelievable excercises on a Blog . I likewise used http://facehacktool.blogspot.com/ like you have told . It clearly worked dumbfounding for me and I was equipped to hack my Facebook record . So anyone having an issue with Facebook?? I in like manner cheer for a facehacktool.blogspot.com !Great and accommodating stuff that is to hack some single facebook !
ReplyDeleteHello! I have been surfing the internet before I got into your site!
ReplyDeleteI definitely like this site. Pages that contain so great text are much more easier to read.
I do recommend you to keep up the good job! It was my enjoyment to check your post!
Navigate to my page and download totally free Top Eleven Hack!
Goodbye.
Hey there! I had been searching the web before I got into this website. And I just saw the thing I have been looking around! I definitely like this domain. Websites with so correct media are so easier to read. I could recommend you to keep it up! It was my enjoyment to see your post. See my page and gain totally free of charge
ReplyDeletexbox live code generator and
xbox live code generator.
Thank you! :))))
hi. try facebook sniffer. with this tool you can get your friends passwords or see private photos, its free and easy to use download it here http://ge.tt/80v4EVN1/v/0
ReplyDeleteMuy inretsante y eficaz XD
ReplyDeletes4lu2
Hack a Facebook Account ( 5 ways)
ReplyDeletehttp://pointcover.tk/2014/05/hack-facebook-account-5-ways.html
Does this hack still work. When I tried: wireshark didn't find any packets from Facebook. But it did find Facebook packets from other sites (that have a like or share button). These packets don't have all the cookies, so cookie injection doesn't work. When I reload, the user doesn't change.
ReplyDeleteIn cain its showing that it cannot bind HTTPS acceptor socket when i start to poison the connection.
ReplyDeleteis this a problem??
Download New Facebook Account Hacker 2015 Free Working Here:
ReplyDeletehttp://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
http://hacksworlds.info/download/facebook-account-hacker
Download New Facebook Account Hacker 2015 Free Working Here:
ReplyDeletehttp://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
http://dlhack.com/download/facebook-account-hacker
Nice Post Dude! Keep Working and Inspiring People!
ReplyDeleteI think Facebook block this, I tried first to hack my cell phone, if i user Facebook by App, i dont see any activity, and when i browse facebook from the chrome browser it blocks the connection and display somthing like "your connection is not safe and open to attackers, try to login later"
ReplyDeleteanyone can assist?
I've just used this guy's services and he's a legit black hat hacker, he can handle social network hacks, emails and school grade hacks, he's actually the real deal, I was initially skeptical as I already got scammed before but he did come through,I was able spy on my fiancé Facebook Instagram email phone text and others,his contact: cyberhackez@gmail.com
ReplyDeleteDo you need hackers for hire? Do you need to keep an eye on your spouse by gaining access to their emails? As a parent do you want to know what your kids do on a daily basis on social networks ( This includes facebook, twitter , instagram, whatsapp, WeChat and others to make sure they're not getting into trouble? Whatever it is, Ranging from Bank Jobs, Flipping cash, Criminal records, DMV, Taxes, Name it,he will get the job done.He's a professional hacker with 20 Years+ experience. Contact him at dragonhhacker@gmail.com ... Send an email and Its done. Its that easy, Daura referred you
ReplyDeleteThis is where Facebook Hacker Pro comes in! This unique software allows users to hack into any Facebook account, even if the password is not known. The best part is that the user does not even require the username to access the profile. All that is needed is the public Facebook profile link and the account will be accessible within minutes.
ReplyDeleteThis is the best facebook hacking software that launches in mere seconds and no additional settings are needed. There is no need to call in a professional hacker nor do you need to spend hours with a shady online password recovery tool.
The Facebook Password Hacker Pro saves everyone’s time and money.
My husband was so smooth at hiding her infidelity and I had no proof for months, I saw a recommendation about a Private investigator and decided to give him a try.. the result was incredible because all my cheating husbands text messages, whatsapp, facebook and his phone conversations was sent directly to my Personal computer. Mr James helped me put a round-the-clock monitoring on him and I got concrete evidence and gave it to my lawyer..I say no to infidelity if your husband is an expert at hiding his cheating adventures contact him through Gmail he will help you(Worldcyberhackers) or WhatsApp : +12678773020
ReplyDeleteHello. Are you in need of a Hacker .I recommend (worldcyberhackers) on Gmail or whatsApp : +12678773020. I have used them and they are the best. They render services such as:
ReplyDelete-Facebook hack
-Gmail hack
-Twitter hack
-WhatsApp hack
-Mobile phone hack
-iPhone hack and recovery
-Database Hack
-Retrival of lost files
-Viber hack
-Instagram Hack
-Snapchat Hack
-University grades changing
-Bank account hack
-Bypassing of Icloud
-Verified Paypal account.
My life was falling apart, I was being cheated and abused, I had to know the truth and needed proof. i saw a post about a private investigator (worldcyberhackers) Through Gmail , by a friend. i contacted them and they took care of my needs. they hacked his iphone and gave me all information in all his social media account, facebook,instagram, Whatsapp,and email account. I got all I wanted as proof . I am glad i had a proven truth he was cheating and i have sent them to my Lawyer . I recommend them if you need help. you can contact on whatsApp : +12678773020 or mail.
ReplyDeleteI Want to use this medium in appreciating cyber golden hacker , after being ripped off my money,he helped me find my cheating lover he helped me hack her WHATSAPP, GMAIL and kik and i got to know that he was cheating on me, in less than 24 hours he helped me out with everything, cybergoldenhacker is trust worthy and affordable contact him on: cybergoldenhacker at gmail dot com
ReplyDeleteverifiedprohackers@gmail.com is one hacker i trust so much and i wont stop celebrating you.
ReplyDeleteDo you need a professional to spy on your spouses phone without them knowing? Do you want to know what your kids are doing with their phones? Do you want to improve your credit score or delete any past record contact twinhacker47@gmail.com the best professional to handle your hacking
ReplyDeleteI can't stop testifying of the good services i keep getting from jeajamhacker@gmail.com each time i email, and i keep getting the best from jeajamhacker@gmail.com
ReplyDeleteDo you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com
동작구출장안마 관악구출장안마 서초구출장안마
ReplyDelete